CYBERTOPICA
by George Anderson, ESEP
We are more interconnected today than ever before. Though we appreciate this technological advancement, we are more vulnerable to theft, fraud, and abuse.Our nation’s security, economy, and basic livelihood is dependent on a stable, safe, and resilient cyberspace.
Roman Keys to Doors or Lockers
I read articles in the New Yorker magazine, the USAF Air University Review, and several Northrop Grumman Company pamphlets that are soberly defining the problem and recommending solutions to Cybersecurity issues. My first reaction to reading much of this is to wonder how we got ourselves in such a vulnerable position so quickly. Are we so vapid that we designed, developed, and now operate, networks that legions of script kiddies around the world can exploit largely unopposed and unidentified?
The sky is falling crowd always tells a good story but I have utmost confidence in the long-term stability of our infrastructure. My confidence is based on the history of technical progress and more specifically on the ubiquitous history of locks. We have a great deal more insight into the life cycle of locks than of information technology.
Mechanical locks are known to predate the ancient Egyptians and have been continually improved as new materials and manufacturing methods became available. The basic principles of operation are notably common and a person trained in lock picking today is right at home manipulating a lock dating from antiquity.
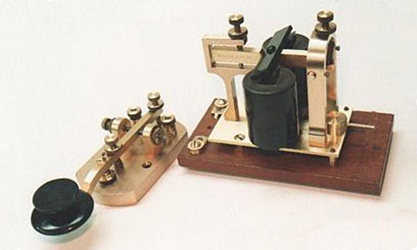
By comparison, the first modern network could be considered the telegraph. Even by today’s standards this system had a number of admirable advantages: it was simple, standardized, and completely interoperable. Added to this, the user interface was easy to learn and required mastery of only simple repetitive skills.
To explain further, the telegraph key and sounder were the standard user interface that when connected to a single wire and a battery constituted the network. Any number of user interfaces could be connected and the control of traffic was based only on operator protocol. Any person attaching his key and sounder to “the wire” could read and send traffic. This dictated that some sort of message encryption was needed and indeed many commercial systems were developed over the lifecycle of the telegraph to satisfy this requirement.
The hacker problem really began when systems evolved to the point where the human interface was reduced and many actions were made autonomous. This got even worse when processing and control capabilities were able to transit the network in addition to message traffic without human participation or notification.
The internet protocol network is currently the ultimate example of system autonomy and provides an opportunity for any participant to maliciously control or operate components of systems owned and operated by others.
Human intervention could mitigate some risks but the speed of data flow on today’s networks requires automation to successfully watch over the performance of existing systems.
What, then, do locks have to teach us about the future of the Internet?
At least six items come to mind.
Historically, we have learned that improving lock security requires expensive, complex and constantly changing designs.
Locks adopted an encryption system that had to be easy to implement, standardized for ease of logistics support, and maintainable by existing skill sets.
Locks were routinely compromised “picked” by experts shortly after being put in service.
The number of expert lock picks was always small in relation to those who imitated their methods and were able to duplicate their success.
The mature state of the lock industry today consists of multiple tiers of lock design based on the vulnerability to picking. Most household locks are medium security based on a tradeoff between cost and the estimated population of imitators who can successfully attack the lock. If a high value location needs protection, then the lock must exclude all imitators and delay, but not defeat, the expert.
The overall lesson learned from locks is: the determined expert can be delayed but almost never defeated. Contrast the few experts to the vastly more numerous imitators and the associated risk analysis points to a medium design as the most useful class of locks.
If this evolution comparison is valid, the solution to the Cyber threat will be a never-ending expansion of our knowledge of vulnerabilities and constant improvement of the corrective tools and processes just as we have seen in the extended development cycle of the lock.